| Home | Projects | Articles | Apophthegm | About |
Capture The Flag (CTF) - Linux Binary Exploitation Challenges Lab
Basic Knowledge Requirements
- Linux (Ubuntu, Parrot Security or Kali Linux is recommended)
- Linux security features (RELRO, Canary, NX, PIE & etc)
- GNU Debugger (GDB)
- GDB Plugins (gef, pwndbg & etc)
- Assemble Language knowledge (optional when Ghidra or IDA is in force)
- Ghidra or IDA (optional but recommended)
- C Language knowledge
- Python Language (Python 3 is recommended)
- Exploit Development skill
- pwntools (optional but recommended)
Challenges
If you can solve the following challenges, please let me know (Discord @samiux#3445).
Linux Binary Exploitation (Pwn) Challenges Lab
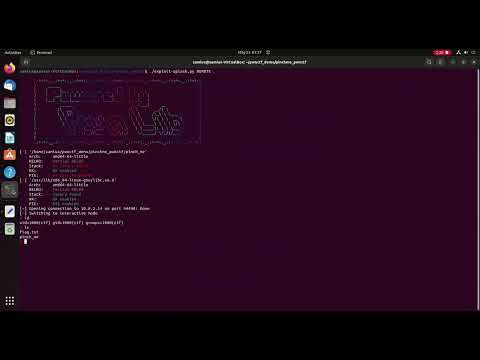
PwnCTF 22.04 is developed on CTFd Framework. The challenges are mainly designed for Pwnable and Practical purpose. Difficulty is basic to intermediate level. No heap exploitation is involved.
PwnCTF 22.04 is based on Glibc 2.35 (Ubuntu 22.04 LTS). There are a total of 10 challenges.
Usage
Import the ova file into Virtualbox (or VMWare) and access the control panel at the server IP address on port 8000 with browser (e.g. http://192.168.56.50:8000). It is well tested on Virtualbox. Network interface is “Bridged Network” by default. Please change the type of network interface on Virtualbox when necessary. Please register at the control panel page for the challenges.
WARNING - This lab is vulnerable and do NOT allow it to be connected to the internet.
Download
-
sha256 : 1857e630706605b9e027ef08968dc57816dff0ade018fb5593aafcdbf51256c1 – PwnCTF 22.04_v20230202.ova (Glibc 2.35)
Changelog
- May 20, 2022 - Version 2022.0 – First released
- May 21, 2022 - Version 2022.1 – Some improvement
- May 21, 2022 - Version 2022.2 – Increase 5 more challenges, a total of 10 challenges
- Aug 19, 2022 - Version 2022.3 – Modify the Virtualbox settings for better implementation experience
- Sep 25, 2022 - Delete Glibc 2.31 version (PwnCTF 2022)
- Oct 15, 2022 - Version 22.04 – Based on Ubuntu 22.04 LTS (GLib 2.35)
- Oct 25, 2022 - Version 20221025 – Updated Ubuntu
- Nov 04, 2022 - Version 20221104 – Updated Ubuntu
- Dec 13, 2022 - Version 20221213 – Updated Ubuntu
- Dec 15, 2022 - Version 20221215 – Minor fixed
- Jan 06, 2023 - Version 20230106 – Reduced OVA file size
- Jan 22, 2023 - Version 20230122 – Update Ubuntu
- Feb 02, 2023 - Version 20230202 – Update Ubuntu and reduced OVA file size
Demo
Tutorials & Writeups
Writeups
Tutorials
- pwn.college - Basic concept in Videos
- CTF pwn tips
- CTF Wiki - Chinese
Books
从 0 到 1 - CTFer 成长之路– Nu1L 战队 编著 (ISBN 978-7-121-37695-5)CTF 竞赛权威指南 - Pwn 篇– 杨超 编著 (ISBN 978-7-121-39952-7)
Bonus
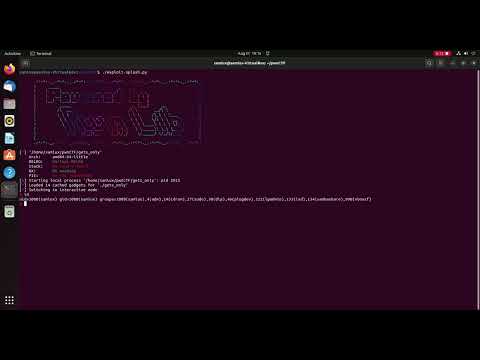
Challenge : gets_only (Linux binary)
Description : Oh! Only gets() in the binary!
File : gets_only
sha256 : 65075f0f30bbd5561ca80aa57c645c7b31af4b49b6f8764575fca4b44989cb1c
Author : Samiux
Date : August 21, 2022
Demo
| Home | Projects | Articles | Apophthegm | About |